Elite
Cyber Intelligence Agency, llc
Private Elite Cybersecurity Services by Invitation
Identify - Protect - Detect - Respond - Recover
Security by Design

Defense in Depth
Application and data security
Host security
Network security
Physical Security
Policy and procedures
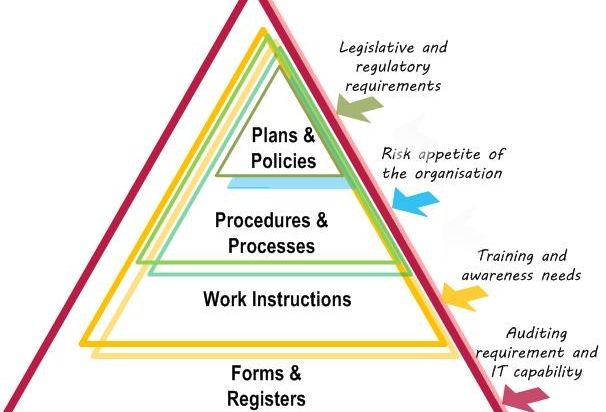
Security Documentation
Documentation is a critical and must not be ignored when it comes to security.
Internal documentation should be prepared with the goal to provide full understanding of the complete networking infrastructure.

Promote Privacy
Organizations should never allow their products or systems to compromise the privacy of the users.
